Wifi Protected Setup: wifi protected setup Risks and Safer Network Alternatives

Wi-Fi Protected Setup (WPS) was dreamt up to make connecting new devices as simple as pressing a button, saving us all from typing in long, complicated passwords. Think of it like a universal keycard for your building—incredibly convenient, but a massive security risk if it ever falls into the wrong hands. This trade-off between convenience and security is where the real problems begin.
The Hidden Dangers of Easy Wi-Fi Access

Let's face it, connecting a new device to a Wi-Fi network can be a bit of a chore. You have to find the network name, squint at the tiny print on your router to find the password, and then carefully type it all in. Wi-Fi Protected Setup was introduced way back in 2006 to solve this very problem, offering what felt like a magical shortcut to get online.
The goal was simple: make life easier for everyday users who were getting tangled up in increasingly complex security settings. In creating this "easy button," however, the system introduced fundamental design flaws that security experts have been warning us about for years. This is the classic tale of initial convenience versus long-term security.
Understanding the Core Concept
At its heart, WPS is a network authorisation standard that lets you add devices to a secure wireless network without ever typing in the password. Instead of manual entry, it relies on much simpler methods to authenticate a device. The two you'll see most often are:
- Push-Button Connect (PBC): You press a physical or virtual button on your router and then, within a short two-minute window, you do the same on the device you're trying to connect. Simple.
- PIN Entry: The router or your device generates an eight-digit PIN that you enter on the other end to establish the connection.
While both seem straightforward, the PIN method, in particular, contains a critical vulnerability that attackers can exploit with relative ease. Getting to grips with these methods is the first step toward realising why WPS is often a liability, not a help.
Why This Matters for Your Business
For IT administrators in hospitality, retail, or even multi-tenant housing, the risks that come with a Wi-Fi protected setup are massively amplified. A single compromised access point can expose sensitive guest data, internal business systems, and create a pathway for widespread network breaches.
The reality is that while most people use passwords, their understanding of the security protecting them is often paper-thin. A 2023 survey revealed that while 97% of UK users secure their home Wi-Fi with a password, a staggering 65% were unfamiliar with the actual security standards like WPA2 that keep them safe.
This knowledge gap is exactly why relying on outdated convenience features is so dangerous. Building a truly secure network means moving beyond these shortcuts and adopting modern, safer alternatives. If you're interested in boosting your security knowledge, our guide on staying safe while using public Wi-Fi is a great place to start.
To understand why Wi-Fi Protected Setup can be such a liability, we need to look under the bonnet at how its connection methods actually work. Think of them as different ways to unlock a door—some are sturdier than others, but one of them has a fundamentally broken lock. The whole system was designed for simplicity, letting devices join a network without the faff of typing in long, complicated passphrases.
This convenience comes from a few different approaches, but the Push-Button and PIN methods are the ones you’ll see most often. Each is meant to create a trusted link between a new device (like a printer or smart TV) and your router, but they go about it in very different ways. By breaking down how they operate, we can see exactly where the security risks creep in.
Push-Button Connect: The Two-Minute Open Door
The most common and visually obvious method is Push-Button Connect (PBC). It’s designed to be as simple as it sounds.
Imagine your router is a bouncer guarding an exclusive club. Normally, you need the exact password to get in. With PBC, pressing the WPS button on your router is like telling the bouncer, "I'm expecting a guest. Let the very next person who shows up in the next two minutes in, no questions asked."
You then press the matching WPS button on your new device. That device strolls up to the "bouncer" within that short timeframe, gets waved straight through, and is automatically handed the network keys. It's quick and works great for gadgets without keyboards, but it also creates a brief window where any device in range could potentially slip in if it also kicks off a WPS request at the same time.
While PBC is generally seen as safer than the PIN method, its security hangs entirely on how short that connection window is. An attacker who is physically nearby and times their attempt just right could theoretically gain access.
The PIN Method: A Flawed Combination Lock
The second main method uses a Personal Identification Number (PIN). On the surface, this sounds more secure—a PIN is a type of password, after all. Unfortunately, the way it was implemented is the source of the most severe WPS vulnerability. In this setup, the router has a static, eight-digit PIN that can't be changed, often printed right on a sticker on the device itself.
To connect a new device, you enter this PIN into its software. The device then presents this PIN to the router. If the numbers match, the router grants access and shares the full Wi-Fi password.
Herein lies the critical flaw, which we'll dig into in more detail later. The process itself is straightforward, but the verification happening behind the scenes is dangerously weak. This weakness turns what looks like a secure combination lock into one that can be cracked with alarming speed.
Other, Less Common WPS Methods
Beyond these two main options, the Wi-Fi Alliance also specified a couple of other methods for Wi-Fi Protected Setup. These were designed to use newer technologies but never really caught on.
- Near Field Communication (NFC): This method requires you to physically bring the new device right up to the router. By tapping the two NFC-enabled devices together, they can securely swap network credentials without any button pushes or PINs.
- USB Flash Drive: An older, clunkier method involved saving the network's configuration file from the router onto a USB stick. You would then plug this drive into the new device to transfer the settings.
While these methods are inherently more secure because they require a physical action or proximity, their lack of universal support meant they were rarely implemented. As a result, the vulnerable Push-Button and PIN methods became the de facto standards for WPS connections.
Uncovering The Critical Flaws In WPS Security
While a simple connection method sounds great on paper, the reality of Wi-Fi Protected Setup security is deeply troubling. The protocol’s most glaring weaknesses aren't just minor bugs you can patch; they're fundamental design flaws baked right into its core. These flaws turn a feature built for convenience into a major liability for any network it’s enabled on.
The main culprit is the PIN method. On the surface, an eight-digit code seems secure enough. After all, there are 100 million possible combinations (10^8), which should take ages to guess. The problem is, the system doesn't actually check the PIN as a single, eight-digit number.
Instead, it makes a catastrophic error in how it validates the PIN. The router checks the code in two separate halves. First, it looks at the first four digits. Then, it validates the next three. That eighth and final digit? It's just a checksum—a mathematical value calculated from the first seven that an attacker's software can figure out on its own.
The Brute-Force Shortcut
This two-step validation process is what blows the doors wide open for an attacker. Instead of trying up to 100 million combinations, they only need to guess the first half (10,000 possibilities) and then the second half (1,000 possibilities).
This seemingly small design choice reduces the total number of required guesses from 100,000,000 to a mere 11,000. It's the difference between trying to crack a bank vault and guessing a four-digit bicycle lock.
This vulnerability means an attacker doesn't need sophisticated gear or insider knowledge. All they need is time and to be physically close enough to your network. It wasn't long before specialised, freely available software tools were created to exploit this exact weakness.
Tools That Exploit WPS Flaws
The discovery of this design flaw led directly to the development of tools that automate the whole attack, making it accessible to anyone with a compatible wireless card and a bit of technical curiosity. Two of the most infamous tools are:
- Reaver: This was one of the first and most famous tools designed for WPS brute-force attacks. It methodically churns through all 11,000 possible PINs until it finds the right one.
- Pixie Dust Attack: A later, more efficient evolution. The Pixie Dust attack can sometimes crack the correct PIN in seconds or minutes, rather than hours, by exploiting weaknesses in how some routers generate their "random" numbers.
Once the correct PIN is found, these tools can retrieve the network’s actual WPA/WPA2 password, giving the attacker full access. Even with a long, complex Wi-Fi password, the WPS PIN vulnerability acts as a weak back door, rendering your primary password completely useless.
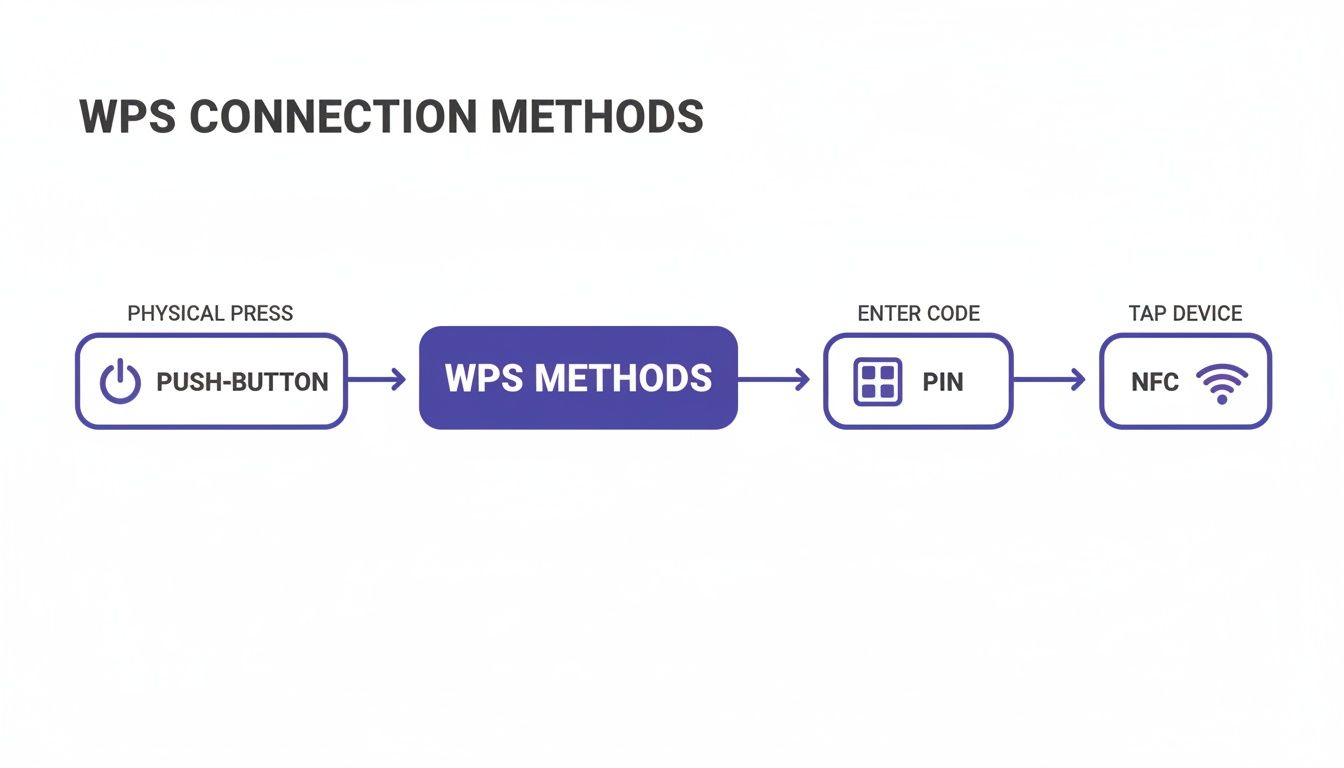
This flowchart illustrates the different ways to connect using WPS. While Push-Button and NFC offer alternative paths, it's the underlying mechanics of the PIN method that create such a significant security risk.
To give you a quick overview of how these methods stack up, here’s a simple breakdown.
WPS Methods And Their Associated Risks
Each method was designed for ease, but as you can see, this convenience often comes at the expense of robust security, with the PIN method being the most critically flawed.
This problem is only getting bigger with the explosion of smart home devices. According to a 2022 techUK report, 77% of UK adults now own at least one smart device, many of which rely on simple setup methods like WPS. This growth exposes countless IoT gadgets, from security cameras to baby monitors, to these well-documented attacks—a huge concern for businesses like hotels managing smart TVs or locks in guest rooms. You can learn more about these trends from the full techUK report.
Ultimately, the inherent insecurity of the PIN method isn't something you can fix with a stronger password or a firmware update. It’s a foundational problem that justifies disabling WPS on any network where security is a priority.
Why WPS Is A Major Risk For Businesses
A weak Wi-Fi Protected Setup configuration on a home network is a problem, but in a business environment, it’s a catastrophe waiting to happen. The convenience WPS offers is completely overshadowed by the amplified risks it introduces in commercial settings like hotels, retail stores, and managed residential properties.
For a business, a network breach isn't just an inconvenience; it's a direct threat to operations, customer trust, and financial stability.
Imagine a hotel where guests expect secure, private internet access. If just one access point has WPS enabled, an attacker sitting in the car park could brute-force the PIN in a matter of hours. Once inside the guest network, they could launch man-in-the-middle attacks to intercept unencrypted data, capturing everything from personal emails to credit card details as guests browse online. The fallout from such a breach would be immense.
The Amplified Impact In Commercial Environments
In a commercial setting, the stakes are significantly higher. A single compromised access point can serve as a gateway to the entire corporate network, depending on how the network is segmented.
Consider a retail chain where point-of-sale (POS) systems, inventory management, and staff communications all run on the same internal network. If a single, forgotten router in a stockroom has an active WPS PIN, an attacker could breach it. This could lead to:
- Data Theft: Gaining access to sensitive customer payment information, loyalty program data, and employee records.
- Network Eavesdropping: Monitoring internal communications and capturing proprietary business information.
- Service Disruption: Launching attacks that could take down payment systems or disrupt supply chain logistics, leading to immediate financial losses.
The potential for reputational damage is just as severe. A public announcement that customer data was stolen due to a basic security oversight can erode years of customer loyalty overnight. In today's market, trust is a currency that businesses cannot afford to lose.
The risk isn't just theoretical. Many legacy or consumer-grade devices, sometimes installed without proper IT oversight, come with Wi-Fi Protected Setup enabled by default. This creates a hidden but significant vulnerability within an otherwise secure infrastructure.
Building The Business Case For Disabling WPS
For any organisation responsible for managing public or private Wi-Fi, disabling WPS should be a non-negotiable, day-one security policy. The operational risk far outweighs any minor convenience it might offer for connecting a stray printer or smart device.
The argument is straightforward: the protocol is fundamentally broken, and no amount of network monitoring can fully mitigate the risk of a swift brute-force attack. Think of it like leaving a faulty, easily picked lock on a fire escape door. While you may have high-tech security on the main entrance, that one weak point undermines the entire system.
Real-World Scenarios And Consequences
The scenarios are alarmingly common. A managed student housing complex might use consumer routers in each unit, all with WPS enabled. A single compromised unit could give an attacker a foothold to snoop on the traffic of hundreds of other residents.
Similarly, a pop-up retail kiosk or a temporary event network might be set up quickly using off-the-shelf hardware. The focus is on getting online fast, and security features like disabling WPS are often overlooked. This creates a perfect opportunity for attackers targeting high-traffic public areas.
Ultimately, the convenience of a Wi-Fi Protected Setup is a relic of a different era. Modern business networks demand robust, scalable, and verifiable security measures. Relying on an outdated and compromised protocol is an unnecessary gamble with your data, your reputation, and your customers' trust.
Practical Steps To Secure Your Network From WPS Attacks
Knowing about the deep-seated flaws in Wi-Fi Protected Setup is one thing, but taking decisive action is what actually keeps your network safe. For any IT administrator, the following steps offer a clear, actionable roadmap to shut down WPS vulnerabilities and harden your wireless infrastructure.
The goal is simple: eliminate the threat entirely.
The single most effective action you can take is to disable WPS on every single one of your routers and access points. It’s often switched on by default, even on professional-grade hardware, creating an immediate and completely unnecessary risk. Turning it off closes the most common attack vector tied to this flawed protocol.
Finding And Disabling The WPS Setting
Hunting down the WPS option in your device's admin panel is usually straightforward, though the exact spot varies between manufacturers. Generally, the process looks something like this:
- Access Your Router's Admin Panel: Pop open a web browser and type in your router's IP address. This is usually something like
192.168.1.1or192.168.0.1. - Log In: Use your administrator username and password to get into the configuration interface.
- Navigate to Wireless Settings: Look for a menu labelled "Wireless," "Wi-Fi," or "WLAN." You’ll often find an "Advanced" or "Security" sub-menu inside.
- Locate and Disable WPS: Find the toggle for Wi-Fi Protected Setup and switch it to "Disabled" or "Off." Make sure you save your changes before you log out.
For organisations with a whole fleet of access points, this process has to be repeated for every device. Centralised network management platforms can make this much easier, often letting you disable WPS across all your hardware from one dashboard.
By turning this feature off, you’re effectively removing the vulnerable PIN back door. From now on, every connection will have to authenticate properly using your main network password.
Essential Network Hardening Steps
Disabling WPS is a great start, but you should also layer on several other security best practices to build a more resilient network. These extra defences help protect against a much wider range of threats, not just those targeting a wifi protected setup.
- Keep Firmware Updated: Always check for and install the latest firmware updates for all your network gear. Manufacturers frequently release patches to fix newly discovered security holes, improve performance, and boost stability.
- Implement Network Monitoring: Use network monitoring tools to keep an eye on connection attempts and general traffic. Strange patterns, like a storm of failed login attempts from one device, could be a red flag for a brute-force attack in progress.
- Use Strong WPA3 Encryption: If your hardware supports it, upgrade your network security to WPA3. It’s the modern standard for a reason, offering far better protection against offline password-guessing attacks. For even more advanced security, it’s worth exploring the benefits of 802.1X authentication, which provides powerful, individualised access control.
Taking these concrete steps allows you to move past the inherent risks of WPS for good. By disabling the feature and reinforcing your network's defences, you can build a more secure and reliable wireless experience for your users and protect your organisation's critical data.
Exploring Modern and Secure Wi-Fi Alternatives

Given the serious risks that come with any form of Wi-Fi Protected Setup, it’s crystal clear that businesses need a better way to manage network access. Fortunately, the world of wireless security has moved on. Modern authentication technologies deliver far superior protection without making life difficult for your users, giving you the best of both worlds.
Stepping away from the vulnerabilities of WPS means embracing robust, modern standards built for today's security landscape. These alternatives don't just shield your network from brute-force attacks; they create a more professional and seamless connection for guests and staff. For anyone looking to leave the risks of WPS behind, exploring secure Wi-Fi alternatives, such as adopting modern mesh WiFi systems like Eero Pro 6e, is the critical first step.
Embracing WPA3 and Simultaneous Authentication of Equals
The most direct upgrade from older security protocols is WPA3 (Wi-Fi Protected Access 3). This standard brings a powerful new feature to the table called Simultaneous Authentication of Equals (SAE), which completely changes how devices join a network. You can think of it as a secret handshake that happens before any sensitive information is exchanged.
Unlike the flawed PIN system in WPS, SAE establishes a secure, encrypted channel between the device and the access point before the password is even sent. This makes it incredibly tough against the offline dictionary attacks that plague older standards. Even if an attacker manages to capture the connection handshake, they can't just go away and guess the password later.
This level of protection is vital for any business that handles sensitive information, ensuring that even if a password isn’t Fort Knox-level complex, the connection itself remains locked down tight.
The Future is Passwordless with Passpoint and OpenRoaming
For venues with high foot traffic—think hotels, shopping centres, or airports—the perfect connection is one that requires zero effort from the user. This is exactly where technologies like Passpoint and OpenRoaming shine, creating a truly seamless and secure password-free Wi-Fi experience.
These systems let a user's device connect to a participating network automatically and securely, without ever seeing a login portal or typing in a password. The device is authenticated using a digital certificate or existing credentials (like a mobile carrier profile), which means the connection is encrypted and secure from the very first packet.
This approach gets rid of the security headaches of open networks and the user friction of captive portals, delivering a premium, secure-by-default experience. It's like having a VIP pass that works automatically at thousands of venues around the globe.
Advanced Security for Enterprise Environments
In a corporate or multi-tenant building, security demands are even higher. Here, modern networks often depend on advanced authentication methods that link network access directly to a user's identity, providing fine-grained control and visibility over who is doing what.
Key technologies in this space include:
- Certificate-Based Authentication: Instead of a shared password, each user or device gets a unique digital certificate. This acts like a non-transferable digital ID, granting access only to authorised individuals and their devices.
- Single Sign-On (SSO) Integration: By connecting with identity providers like Entra ID, Google Workspace, or Okta, network access can be governed by existing company logins. When an employee leaves and their account is shut down, their Wi-Fi access is revoked instantly.
Solutions like Purple are built on these modern, secure principles. By using Passpoint, certificate-based methods, and SSO integrations, Purple offers a secure, frictionless alternative to outdated systems like WPS. To dig deeper into how identity can lock down your network, you might be interested in our complete guide to identity-based Wi-Fi security. This approach lets businesses provide both ironclad security and an effortless journey for their users.
Got Questions About Wi-Fi Protected Setup?
Even when you know it's flawed, Wi-Fi Protected Setup can still be confusing. Let's clear the air and tackle some of the most common questions to make sure your network stays secure.
Is The Push-Button Method Safer Than The PIN Method?
Yes, the push-button method is less risky than the PIN, but that's a bit like saying one back door is slightly less open than another. It's not truly secure.
Its only protection is the very short, two-minute window it opens for a new device to connect. An attacker would have to be physically close by and have perfect timing to exploit this brief opportunity. The PIN method, on the other hand, can be brute-forced from a distance over hours or days. So while push-button is the lesser of two evils, both methods are part of a broken system. The only truly safe move is to disable WPS completely.
Does A Strong Wi-Fi Password Protect Me From WPS Attacks?
Unfortunately, no. A strong, complex WPA2 or WPA3 password is a critical part of your network's security, but it does absolutely nothing to stop a WPS PIN attack.
This is the heart of the problem: the WPS PIN vulnerability is a separate entrance that bypasses your main network password entirely.
An attacker exploiting the WPS PIN doesn't need to guess your Wi-Fi password. Once they crack the eight-digit PIN, the router simply hands them the network credentials. Your carefully chosen password becomes completely useless.
Can I Safely Use WPS For Simple Devices Like A Printer?
This is a common reason people leave WPS enabled, especially for devices that don't have a screen or keyboard for typing in passwords. It might seem like a small risk for a simple device, but it still leaves your entire network exposed.
Even a "simple" device like a printer is an entry point. If an attacker gets access through that printer, they have a foothold on your network. From there, they can try to move sideways to attack more valuable targets like servers, point-of-sale systems, or guest databases. The brief convenience of connecting one device just isn't worth the permanent risk it creates for your whole infrastructure. The only secure option is to turn it off.
At Purple, we believe in replacing outdated systems like WPS with secure, identity-based networking. Our platform uses modern, passwordless authentication like Passpoint and SSO, giving you both ironclad security and a seamless connection experience for your users. Find out how Purple can modernise your network security.